What is SQL injection?
Read our SQL injection examples to understand how SQL attacks work.
Brief Summary
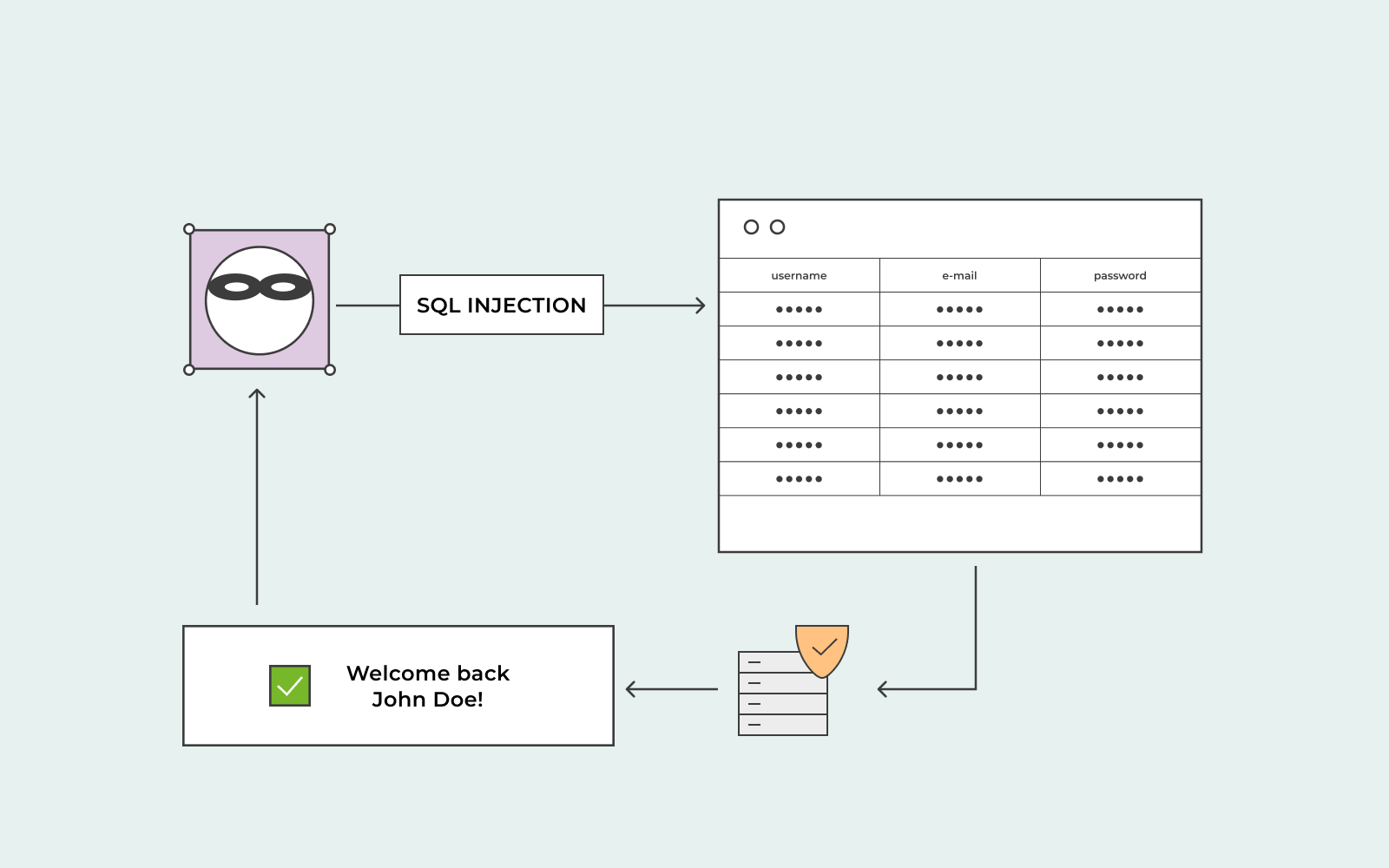
SQL injection is a type of cyber attack where a hacker uses malicious code to manipulate a website’s database and gain access to sensitive information.
A SQL injection attack allows a hacker to see data that they’re not privy to or able to get their hands on. The data is sensitive as it can be data belonging to users or data that the application can access.
What does the hacker want with the data? Commonly, the hacker will delete the data from the web application or change it completely to cause problems and change behaviour.
In some cases, the attacker will perform a SQL injection attack on the web application’s server to compromise its function.
What is the impact of a SQL injection attack?
Many companies are harmed by SQL injection attacks, even large companies. If your company falls victim to a SQL injection attack, it goes without saying that it’ll negatively impact your business. Your company will lose users’ private information, amongst other things, and that is terrible for your company’s reputation. Also, it’s illegal to lose this type of information due to the data protection act. Therefore, it’s essential to take preventive measures to avoid an attack.
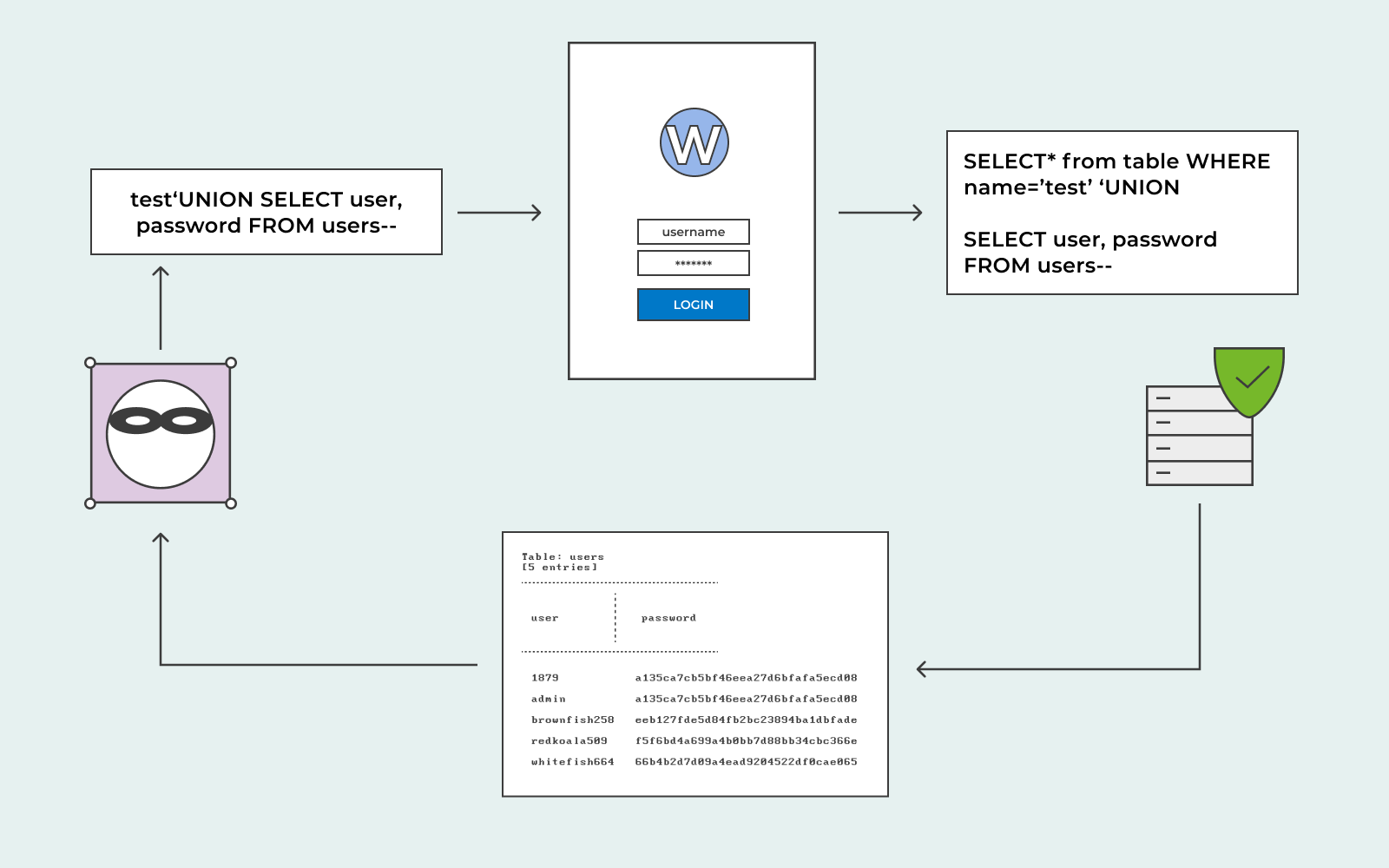
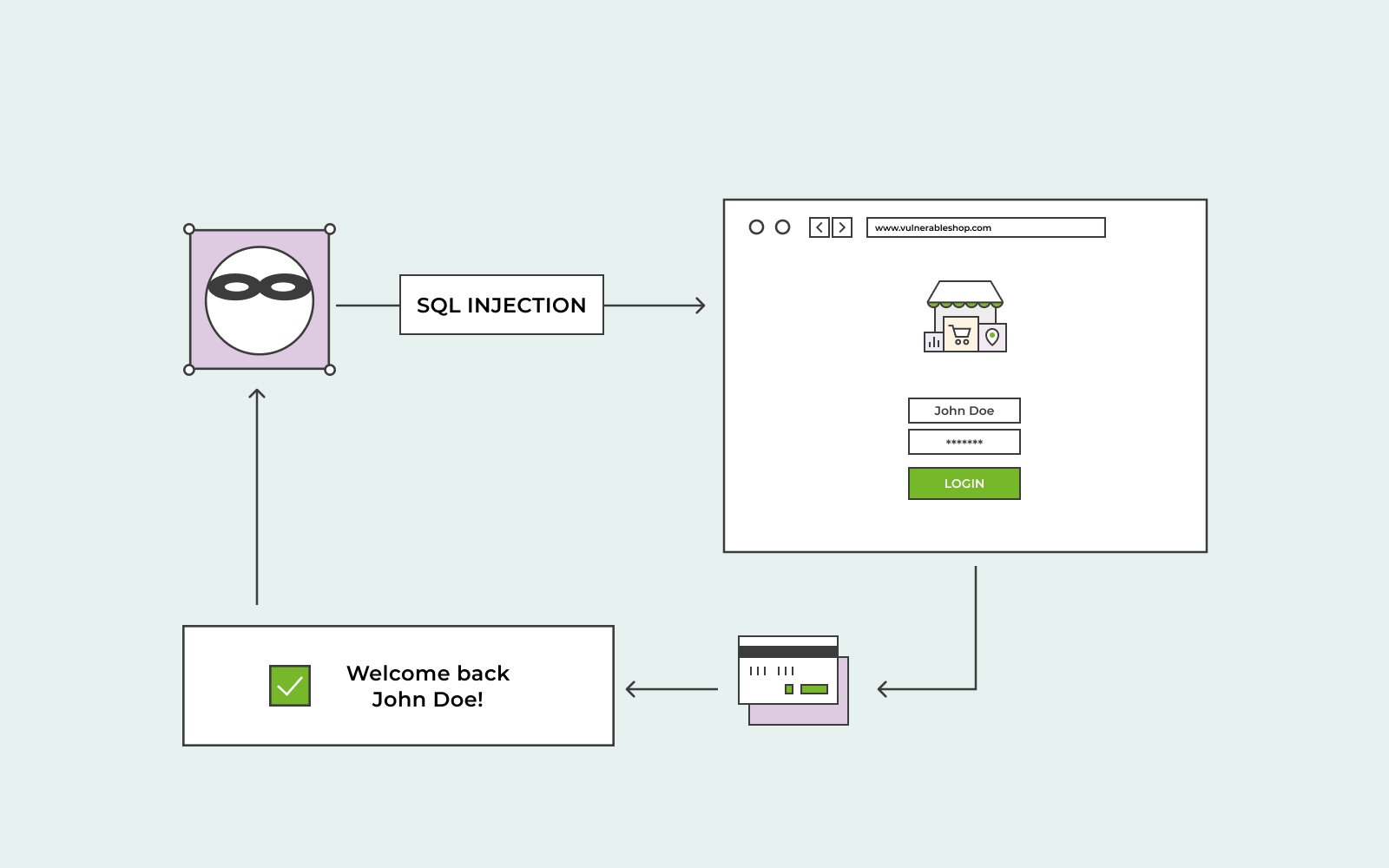
SQL injection example of attack
An example of an attack can be something along these lines. Let’s say that you have an e-commerce website. You have a category dedicated to selling sneakers. A user is interested in purchasing sneakers, so they visit that category on your website. When the user clicks on the category, their browser will request:
https://fake-website.com/products?catgory=Sneakers.
Your web application will make a SQL query in order to receive details of relevant information about that category from the database.
The SQL query will most likely read as:
Select * FROM products WHERE category = ‘Sneakers’ AND released = 1
In this instant, the SQL query is asking the database to return details from the products category you have, specifically, your sneakers category.
Released = 1 is a restriction. It’s 1 there in order to hide products that have not yet been launched. For example, you have other variations of sneakers that you want to release further down the line. The 1 will make sure that they’re not available to the public.
Your web application might not have any way to protect itself from a SQL injection attack. So, an attacker can, unfortunately, attack in a way like this:
https://fake-website.com/products?catgory=Sneakers’–
This will result in a SQL query that looks like this:
Select * FROM products WHERE category = ‘Sneakers’–‘ AND released = 1
The double dash sequence is a comment indicator that indicates that the query is a comment. And if the system believes that the query is a comment, it can’t know that it’s an attack. Subsequently, the double dash will remove the rest of the query (AND released = 1), which will, in return, release information on all your products in your category. Even those that have not been released to the public yet.
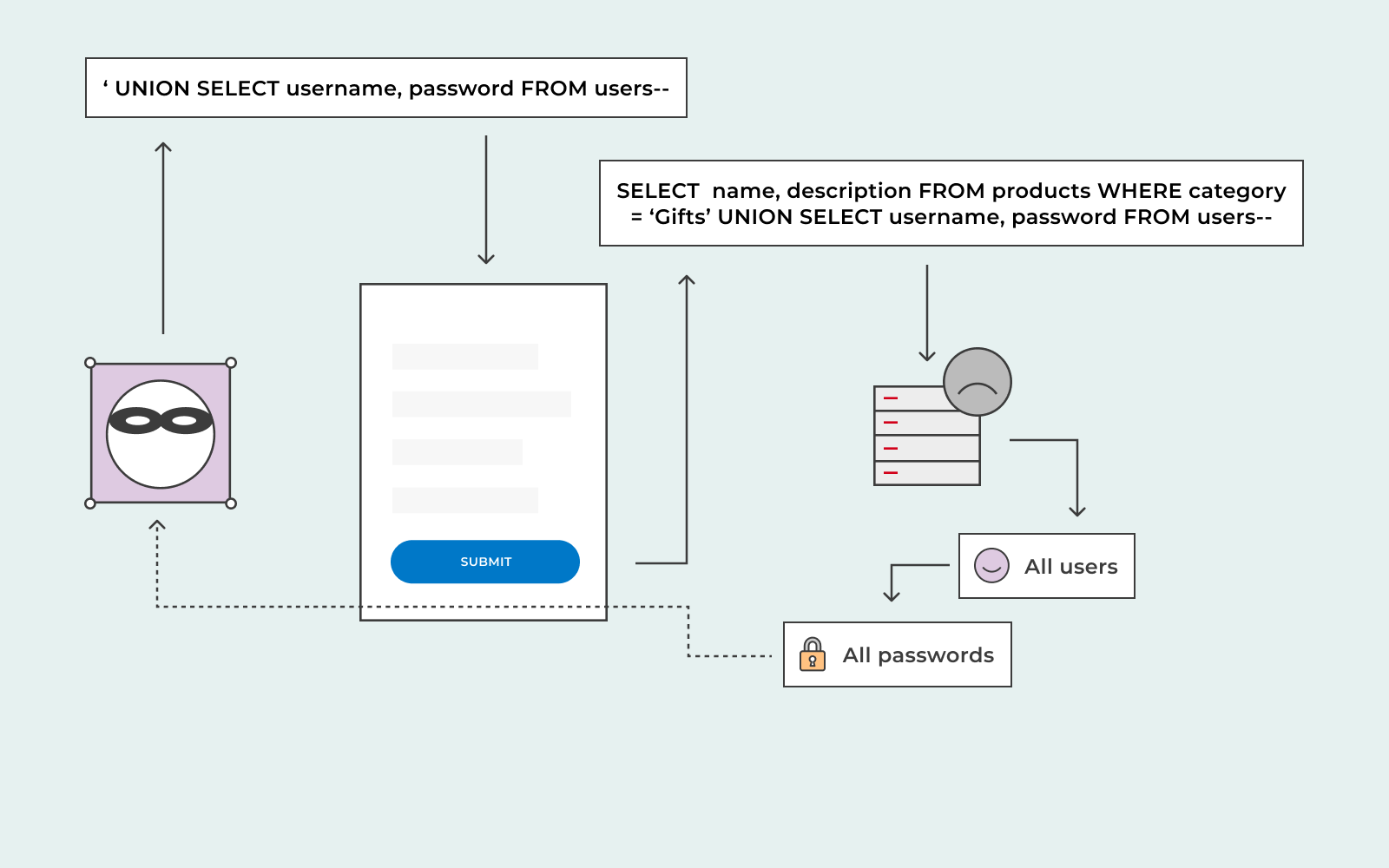
Furthermore, the attacker can send a SQL attack to see everything else you sell on your website; all your other items in other categories.
The attacker will attack thought this way:
https://fake-website.com/products?catgory=Sneakers’+OR+1=1–
This will result in a SQL query that looks like this:
Select * FROM products WHERE category = ‘Sneakers’ OR 1=1–’ AND released = 1
Sending this query will return information on all items on your website.
There are many other ways that an attacker can perform an SQL injection attack. Let’s touch briefly on them.
- Boolean
The attacker will send a SQL query to return a result from the database quickly. By using this Boolean method, the attacker can determine if the result returned was true or false.
- Time delay
The attacker will send a query to make the database wait; it will create a time delay. Using this method, the attacker will know if the query they sent was true or false based on the time it takes the database to respond.
- Out-of-band-network
The attacker can carry out an out-of-band attack if the server the database uses has certain needed features. The attacker will withdraw data through the out-of-band channel and place it somewhere else. This type of attack counts on the server to create a DNS or HTTP request to transfer the private data to the attacker.
SQL injection attacks
The most common SQL injection attacks are in the where clause of a select query. However, it can also happen within different query types. It can be in update statements, insert statements, select statements, and order by clause.
How to prevent SQL injection attacks?
You can take measures already today! The majority of SQL injection vulnerabilities can be found quickly.
- Scanner
Use burp suites web vulnerability scanner. You can use this scanner by setting up tests against every entry point in the application.
You can look for errors, systematic differences, and the application responses you receive.
- Input validation and WAF
Write a code that can identify illegitimate users. However, this is not a bullet-proof method when used alone. It can create a lot of false positives. Implementing this method while also using a web application firewall can be effective. The WAF will filter out SQLI and other online threats.
When the WAF gets the hint of an illegitimate user, it will verify the IP data firstly before blocking the request. Thus, if the IP data has a bad reputation, it will be blocked based on that.
Stay safe out there!
