What is DDoS?
Read all you need to know about DDoS
Brief Summary
A distributed denial-of-service (DDoS) attack is an attack where multiple computers or devices flood a website or server with traffic, overwhelming it and causing it to crash or become unavailable.
A DDoS occurs when your server or network is under a cyber attack. You might wonder what the purpose of a DDoS attack is? It’s to disrupt the regular operation of the network or the server.
The DDoS attack is carried out by sending falsified requests to the network or server to overwhelm it with too much traffic. It disrupts the operation by carrying out this attack, and the website you’re trying to visit will only come up blank.
Basically, it will issue a denial of service to you (whose server has sent a legitimate request) who have clicked on the link and want to visit the website.
Think of a Dos and a DDoS attack as a traffic jam. An accident has occurred, leaving everyone in the traffic at a standstill for hours.
What is a DDoS attack and how does it work?
Let’s say that you own an e-commerce website where you’re selling tasty home-baked cookies. You have repeat customers who enjoy your cookies and the recipes you post on your blog. Let’s also say that on a particular day, your customers are browsing your website simultaneously as an attacker is trying to attack your server. The attacker will use a program to send multiple false requests that make your server believe that you have so many visitors on your e-commerce website that it cannot handle all the traffic.
This is referred to as a DoS attack, leaving your customers with a denial of service. Your server can typically handle a DoS attack because your server is being attacked from only one direction – one attacker. Thus, it’s easier for your server to identify the attacker and close off the attacker’s connection that they use to send falsified requests.
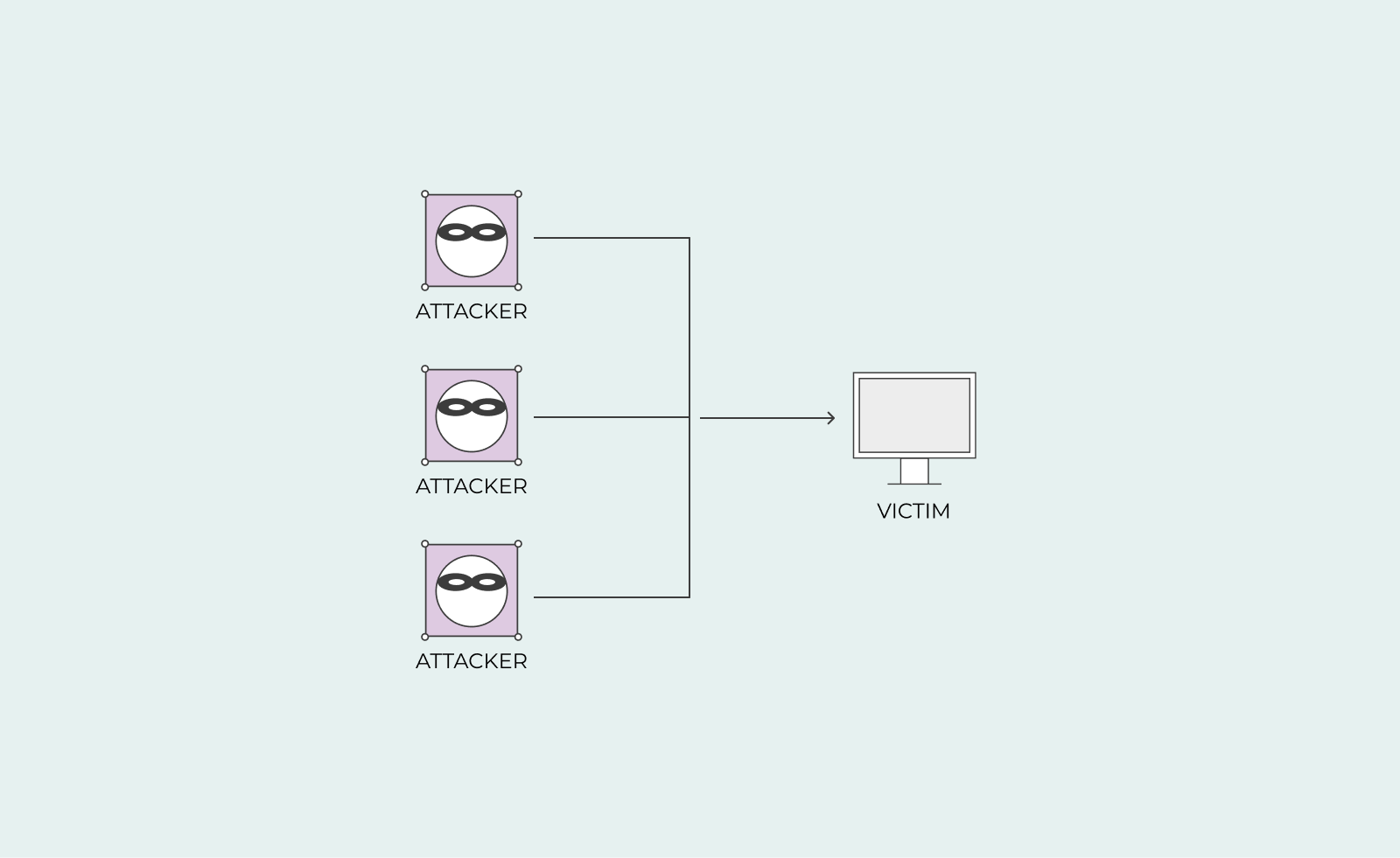
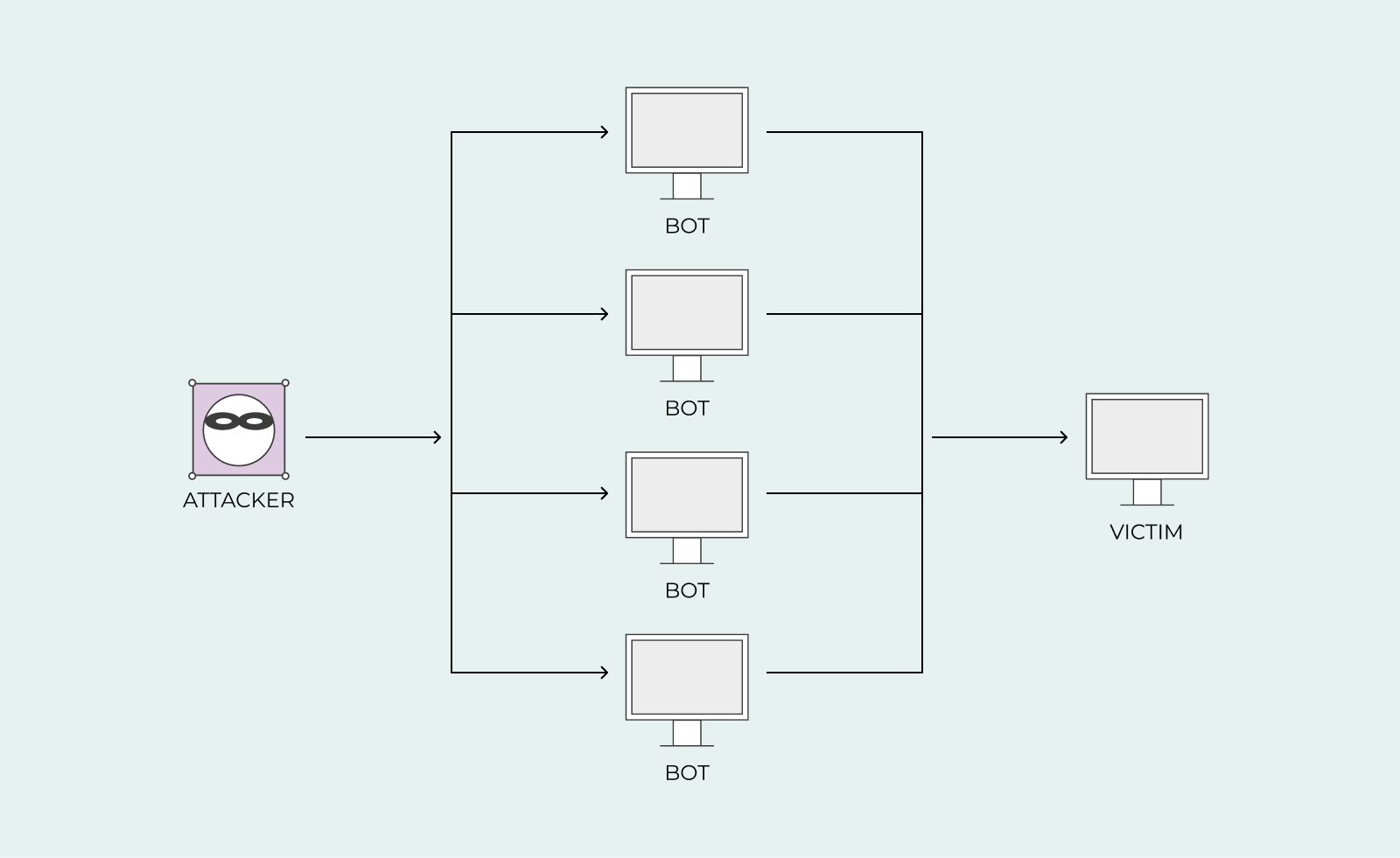
A DDoS attack is when several attackers are attacking your server. Usually, one computer is the leader and communicates and coordinates an attack with other computers around the world. This can become a massive problem as your server will not be able to identify and close the connection easily when they are coming from every direction.
Your server will have to try to close connections with multiple computers. When your server tries to close all these connections, it will overwhelm it. The server will use all the resources it has to complete this task, leaving no resources left.
One of the most significant resources it’ll lose is network bandwidth, which will affect the ‘good’ computers who are trying to enter the site. The good computers being ordinary people trying to visit your website. Your server will deny the ‘good’ computers service because it’s too busy fighting off an attack. The consequences for these ‘good’ computers are that they can’t access your website or they can, but your website will load extremely slow.
What does a DDoS attack look like?
So you might wonder what a DDoS attack looks like? As mentioned above, a DDoS attack is when multiple computers attack a server or a network. Once a DDoS attack begins, it can go on for hours or days. The amount of time a DDoS attack lasts depends on the purpose of the attack. But how do these computers carry out the DDoS attack? They use malicious software. The attacker will use malware that they upload on websites and email attachments with the hopes that someone will visit the website or click on the email attachment.
If you visit a website that has been infected with malware or open the email attachments sent to you, your computer will also become infected with malware without you even knowing. Being aware of phishing emails is very important to avoid a situation like this occurring.
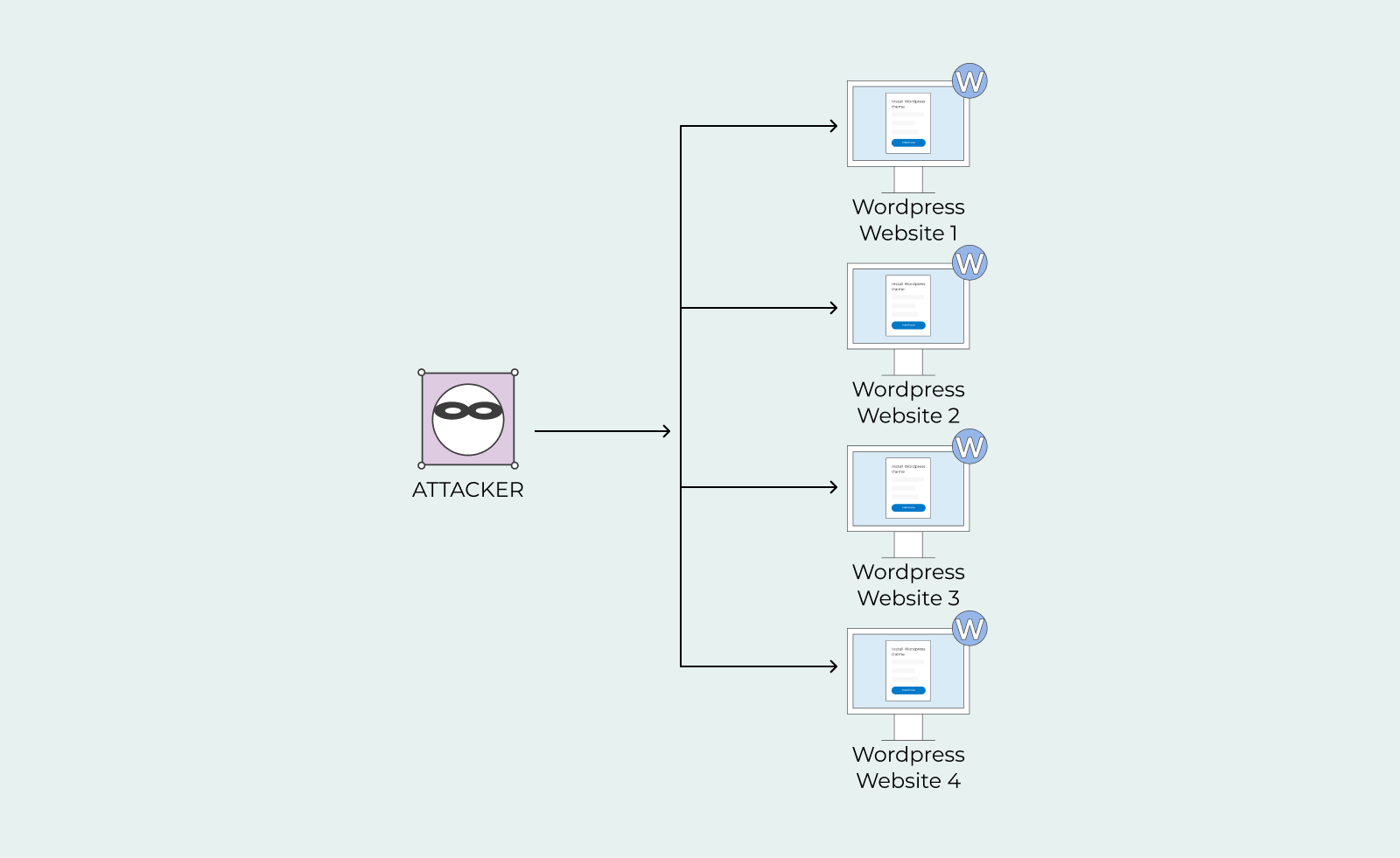
Once your computer is infected with malware, your computer will join all the other computers that have also been infected to create an army. There might be numerous computers infected in this recruited army, and it’s all happening in the shadows, so you wouldn’t know that your computer performs a DDoS attack.
All these computers together become what’s referred to as a botnet. The meaning of botnet is computers infected with malware and controlled as a group without the owner’s knowledge.
The botnet army is not limited to a couple of computers; it can be thousands of computers all controlled worldwide. The attacker who installed the malware on websites and email attachments to start with is also the person who has all the control. Once the attacker wants to attack a server or a network, all the attacker needs to do is send a command to these computers worldwide.
What is the purpose of a DDoS attack?
Why is the attacker doing this? What is the purpose of the DDoS attack? We’ve listed some plausible reasons below.
- Competition
An attacker performs a DDoS attack to get rid of the competition, which in return is because of financial reasons. By implementing a DDoS attack, the attacker is blocking the competitors’ website from doing business.
- Political reasons
It can be perhaps because the attacker does not like a political organisation and wants to damage their server.
- Fun
It can also be that an attacker does this because they find it funny. Maybe they are bored, and this is a way to spend their time. Or perhaps they want to prove to themselves that this is something they can do.
How to prevent a DDoS attack?
We’ve listed a few things that you should consider to prevent a DDoS attack. It’s very hard to fix the damage once the attack has reached completion, so it’s best if you take preventive measures from the start.
- Bandwidth
If your server is on a cloud, you should buy more bandwidth to be safe.
- United Threat Management
Pay the extra money and get yourself a UTM, a better and safer firewall. UTM is a great way to stay secure from malware and all the other viruses and risks worldwide.
- DDoS service
If you really don’t want the risk of a DDoS attack, you can enlist the help of a DDoS protection service. Many companies have services that work with keeping you safe from a DDoS attack.
What is the difference between a DDoS attack and a Brute force attack?
Firstly, what is a brute force attack? A brute force attack is a process of hackers trying to guess their way to logins, passwords, encryption keys etc., hoping that one of their guesses will be the correct one.
A brute force attack is performed to redirect users from a website (that they’ve managed to hack by guessing the password correctly) to their own questionable website.
It can also be a goal of a brute force attacker to steal personal information such as financial information by installing malware.
The difference between a brute force attack and a DDoS attack is in the process and method. However, they both have the same goal: to attack a victim, a website, or a server/network.
